We use them for everything – to communicate with clients and customers, to make hotel reservations, or send a complaint to a store because the product we bought is damaged. But have you ever stopped to think about just how secure your emails are?
And look at how many people from different age groups rely on emails for communication:
- 94% of Gen Z
- 98% of Millennials
- 98% of Gen X
- 95% of Boomers
- and even 90% of the Silent Generation!
Add to it that email marketing was picked as the most effective channel by marketers surveyed in Hubspot’s State of Marketing Report 2022, and you can see why email marketing is thriving, despite so many people predicting email’s death for years.
Why does email security matter?
Unfortunately, emails are also one of the most valuable methods for criminals to attack a company or steal regular users’ personal data. CISCO’s 2021 cybersecurity threat trends report found that about 90% of data breaches occur due to email phishing.
And that’s not the end of worrying news:
- 3.4 billion phishing emails are sent every day
- In 2022, there was a 569% increase in malicious phishing emails and a 478% increase in credential phishing-related threat reports published
- Business email compromise (BEC) attacks increased by 81% in 2022
- Without proper security training, one in three employees will fall for phishing scam
- Only 15% of IT administrators enforce the use of two-factor authentication.
Cybercriminals also take advantage of the fact that people nowadays get so many emails, that they hardly have enough time to carefully read every mail they get and check for spam messages. That’s especially true for employees, who, on average, get 100-120 emails daily. Who has the time to check every email for safety requirements, be it business or personal emails?
So a bit of social engineering and criminals can quickly get them to click on a phishing link or download a malicious attachment. This is in addition to hackers targeting business phones that employees use like VOIP systems.
Fortunately, there are a few easy things you can do to protect your email inboxes – and, this way, also your personal or business data. So let’s look at 8 email security best practices that can make the cybercriminals’ “job” much harder.
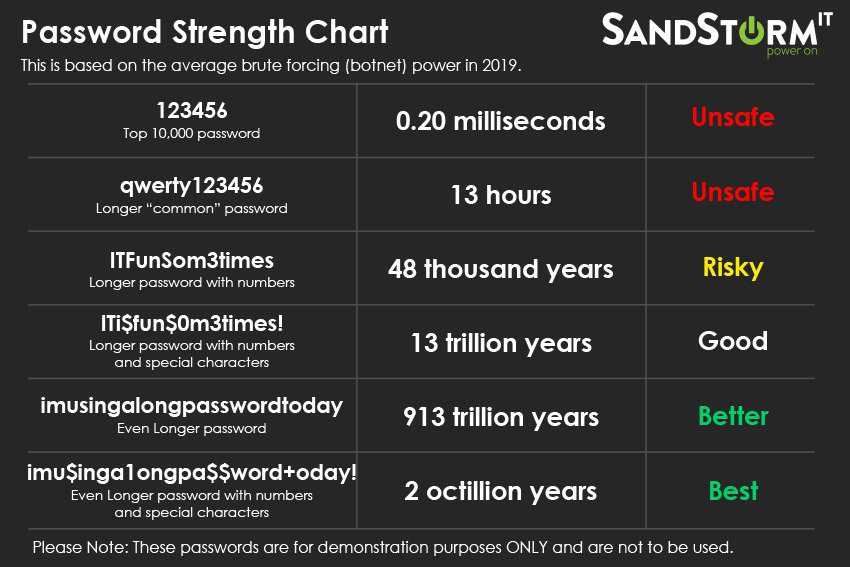
Create strong passwords
Using strong passwords is one of the best ways to defend your email accounts and private information inside those from hackers. Here are some ways to keep your security standards high in terms of passwords:
- Not using any obvious personal information or common words
- Being a mix of letters, numbers, and symbols
- Having at least 10 characters (experts recommend 14-16)
Still, looking at how many online accounts (both private and work-related) we are all using, creating, and then remembering 20 or so complex passwords can be quite tricky.
Here is where password managers tools can be incredibly helpful. These tools can generate unique, extremely hard to brute-force passwords for each application and then store them inside their database – the users then only need to remember one “master password” to unlock the database.
Another popular option now is passphrases – passwords made of a string of words rather than random characters. Since they are typically longer than regular passwords, they are harder to brute-force. Plus, with passphrases, it’s also easier to create memorable but secure passwords for the accounts.
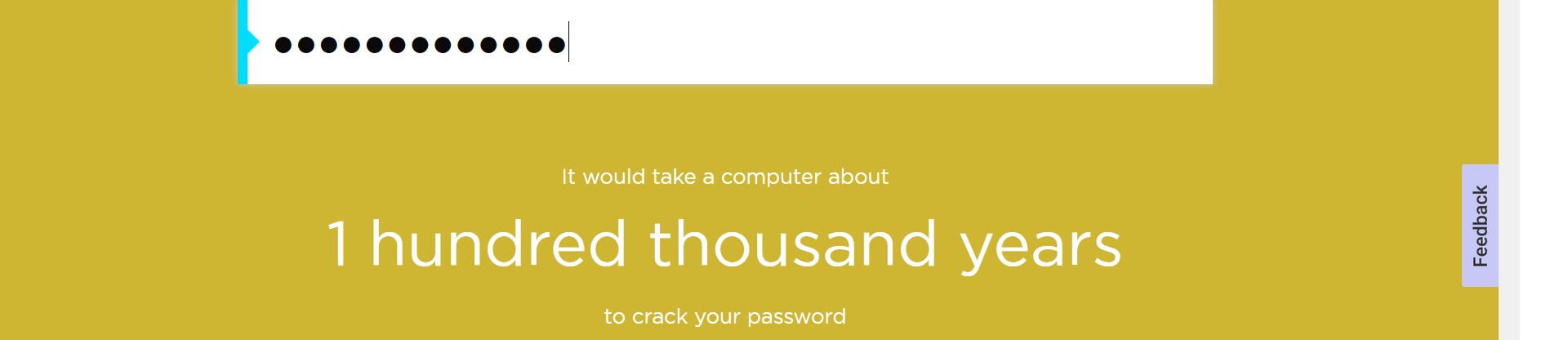
To see how secure your own passwords are, you can use Security.org’s How Secure Is My Password tool. Here’s how it looks for one of our accounts:
Don’t reuse passwords across accounts
Password reuse is another widespread security issue. For example, the First Contact study found that 51% of people use the same password for work and personal accounts.

What’s even worse is that 70% of users who had their passwords breached were still using those!
The reason why this is such a bad idea is simple. Cybercriminals know well just how many people reuse their passwords, so they always check how many accounts they can unlock with one password. For example, if you use one password for 5 personal accounts, then if the password leaks, all 5 accounts will be compromised.
Using the same password for business and private accounts is especially dangerous as in this way, hackers can quickly gain access to your work email inbox – and the data inside it. Enterprise email security is vastly different from the emails you use for personal needs and malicious content for work-related emails is way worse than a Nigerian scam to your personal email.
Use multi-factor authentication
And while we are on the topic of securing accounts – adding an extra verification measure can also visibly boost the security of your account. With 2FA and MFA, even if hackers steal the login and password, they won’t be able to access the email inbox until they confirm their identity through additional security checks – and this might be enough for them to give up.
After implementing 2FA and requiring their users to use it during every login, Google said they saw a decrease in account breaches by 50%.
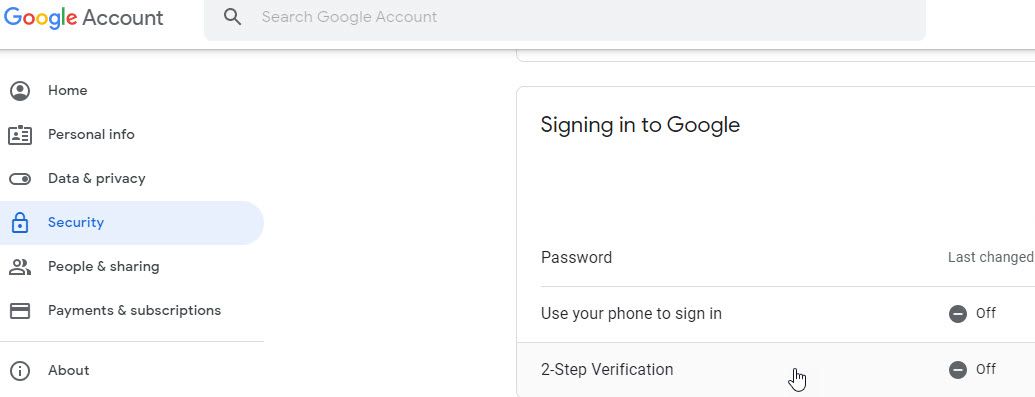
How can you add it to your account, for example, Gmail one? That’s actually quite simple. To secure your personal account with 2FA, you need to do:
- Open your Google Account.
- In the navigation panel, select Security.
- Under “Signing in to Google,” select 2-Step Verification and then Get Started.
- Follow the on-screen steps.
For business accounts meanwhile, you can find the 2FA option in your admin console, under Menu → Security→ Authentication→ 2-step verification. From there, you can also set whether the MFA should be mandatory for all users or just specific groups and what methods they can pick for the verification.
Email systems such as Gmail will flag suspicious activity and ask you to do two-factor authentication before letting you view any email content. If you’re the actual person trying to log in, you can do so in a matter of seconds. This can prevent many email threats.
Train employees on email security best practices
Even the most complicated passwords and several additional security check-ups won’t be of much help though, if employees don’t know or understand why securing their accounts is so important. Verizon Data Breach Report (DBIR) for 2023 found that users’ carelessness was the cause of 98% of the data breaches – and cybercriminals know exactly how to use this to their advantage. Recognizing employees who follow security best practices through employee recognition software can encourage others to stay vigilant and responsible.
Regular cybersecurity training as part of their continuous performance management is an excellent way to teach employees the consequences of a data breach and what they can do to prevent those. You can use those to talk with them about the company’s email security policy, email security threats they might encounter, and recommended best practices for securing their accounts.
For example, you could teach them about the value of email encryption, about not opening suspicious emails or not accessing email through a public wi-fi network. Also, not to open unsolicited emails, to try and use antivirus software, and in general, watch out for unknown senders.
Cybersecurity training is also a great practice to train your employees on how they should react when they notice that a breach has already happened – and who they should alarm about the breach. Consequently, the breach can be contained faster – and so the damage caused by it can also be reduced.
Be wary of email attachments and suspicious links
94% of malware is delivered via email – either through genuine-looking attachments or links to seemingly reputable websites. And while Gmail algorithms and antimalware software can spot and block most suspicious attachments or websites, some of the more sophisticated attacks might still get past the radars.
That’s why regular users and employees should stay cautious when they get emails with attachments or urging them to click on an included link. Here are a few tell-tale signs that the attachment or link might be coming from hackers:
- The file extension doesn’t match the file type (for example, it ends in a double extension, like doc.exe, or it has an executable extension only. You should be especially suspicious if you get attachments ending in exe, jar, or rar/zip extensions).
- The sender’s address is slightly different than the one you can find on their website/your email list – this is a surefire sign of spam emails – see how to stop emails going to spam.
- The email seemingly coming from a trusted source (such as your bank) has spelling, grammar, formatting, or interpunction errors.
- The message urges you to open the attachment or click on the link as soon as possible because otherwise, you might face some consequences (the infamous “Your credit card will soon be blocked” is the best example here)
To stay on the safe side, it’s best to always call the sender to ask them about the emails if you have any doubts and scan all attachments you get for viruses or malware. Or you can just copy the sender name, link, or part of the message and put it into the search engine – other users might already mark it as dangerous.
Regularly update your Antivirus or Antimalware Program
Modern antimalware solutions can protect your devices from numerous threats – viruses, trojans, malware, ransomware, and suspicious websites as well. That is, as long as they are regularly updated. Cybercriminals invent new methods to attack devices and steal data virtually every day – and each day, 560,000 new pieces of malware are detected.
If the antivirus programs you use aren’t regularly updated, then they might overlook the new threat – putting your email account and the entire device at risk.
Most of the popular cybersecurity platforms such as Crowdstrike or alternatives and incident management tools like Opsgenie or alternatives have the option to install those updates automatically though – so if you want to ensure that your platform is always up-to-date, it’s worth ticking this option.
Use email authentication protocols
Implementing authentication protocols for your work domains can also make your accounts much more secure and identify malicious intent through various forms of identification.
Email authentication protocols were designed to prevent phishing attacks, email spoofing, and BEC attacks by verifying whether the email is coming from a legitimate sender. In simpler words, those protocols check whether the newest marketing campaign emails are sent by you or whether someone is impersonating your brand.
Currently, we have three authentication protocols:
- SPF (Sender Policy Framework) – Examines the sender’s IP address to ensure each email comes from a trusted IP address.
- DKIM (Domain Keys Identified Mail) – uses public/private key encryption to sign email messages and prove that the messages weren’t altered.
- DMARC (Domain-based Message Authentication Reporting and Conformance) – ensures that the email meets SPF and DKIM before being delivered.
See the deliverability guide.
By using those protocols, you can reassure your clients and subscribers that your domains won’t fall victim to email spoofing and so the emails they get are definitely coming from you. We mentioned a few other benefits of those protocols in our other article about authentication methods, so you might want to read that as well.
When mailing out campaigns, make sure your lists are clean
Our last tip – regularly clean your email lists.
Okay, you have heard that email list scrubbing can boost your deliverability rates, improve your domain reputation, and give you better ROI, but what does it have to do with security? A lot, actually! By examining the addresses on your email list, you can spot inactive and outdated email addresses but also any suspicious addresses that might belong to spammers – or ISPs, aiming to find and punish the spammers.
If you are found sending your emails to those domains, there’s a good chance that your domain reputation will take a hit – and in the worst case, you might even get blacklisted.
👉 Read more: Email Blacklist Checker: Which One to Choose?
How can you spot all those toxic emails on your list without spending days (or more) verifying them manually though? Bouncer’s email verification tool can lend you a hand here.
Just add your email list (up to 250k addresses) to the app, and Bouncer will show which emails belong to real users, how likely the emails are to bounce but also show you:
- breached or hacked email addresses
- invalid addresses or domains
- spam traps, etc.
Bouncer will also score the toxicity of the emails (from 1 to 5) so you will know which addresses you should remove straight away.
That sounds useful, right? Then, how about using Bouncer for your next email campaign? With a squeaky-clean email list, making your next campaign a success while also protecting your email domain will be easier than ever.

Time to fortify your email accounts
To keep your private and business email account (and the data inside it) away from cyber criminals, you need to take all the safety precautions you can and say goodbye to worrying about malicious activities, potential threats and suspicious messages.
Strong and regularly changed passwords, adding multi – factor authentication, keeping your antivirus tools regularly updating, and also watching out for any phishing or infection attempts are all important when it comes to securing your accounts.
And with fortified account security, you’ll be able to ward off any phishing attack or breach attempt with ease.
FAQ: Email Security Best Practices
How can I secure my professional email account?
The best way to make your account more secure is to use strong and unique passwords for each account you are using – you can use password managers for this. A smart idea is also to enable two-factor (or more) authentication for an extra layer of security. If you are using Exchange Online email, consider implementing a reliable data backup solution for Microsoft 365 to protect against potential data loss or corruption.
How can I identify and avoid phishing attacks?
While they might look exactly like genuine emails at first glance, there are actually a few traits of phishing messages that make them easy to recognize. The most characteristic one is they urgently ask for personal or financial information, threatening that you might face severe consequences if you don’t comply.
When you get such an email (claiming to be from your bank, for example), you should first check whether the sender’s email is correct – criminals typically use emails that resemble reputable domains but have one or more differences (for example, different domain names).
If the email has spelling or grammar mistakes or the logo looks wrong, that should also raise your suspicions.
What is multi-factor authentication, and why should I use it for email?
Multi-factor authentication (MFA) adds an extra layer of security to your email account by requiring two or more different types of authentication factors during login. For example, a password and a one-time verification code, confirmation from a trusted device, or a fingerprint scan.
Using MFA significantly reduces the risk that someone will gain access to your email inbox even if your password gets compromised.
Are there any specific email security practices for businesses?
Creating a cybersecurity policy for business email accounts and conducting regular security awareness training for employees is a great way to ensure that all employees know how they can protect their accounts and devices from cyber threats.
Inside the policy, you can outline how they can create strong passwords, when and how they can use private devices for work, or what the guidelines are for opening received attachments.

